
Premise
The problem with programming in its initial phase was its inconvenience in not being able to collaborate with fellow programmers and bringing better logic and implementation to the fore.
Earlier, software only required annual updates or quarterly maintenance to make sure software was running in the intended manner. Over time, customer demands change, with software being required at every possible situation in life. Software needed to be maintained well, with no inconvenience caused to the customer, due to the software’s failures.
Introduction
With the advent of DevOps, software underwent regular modification to add new features, reducing SD time and making life much easier.
Programmers can now create code, use systems like Bamboo to test it, and integrate it into the software, allowing to make multiple changes to the same, in an agile manner, ensuring fast delivery of code.
Often during the software development phase, the whole necessity of software security is not considered or gets to a point where security can no longer be implemented (during the rollout phase).
Why does security often get weeded out?
This can be put down to reasons such as:-
-
Rewriting and modifying countless lines of code
-
Rewiring condition statements
-
Integrating security mechanisms for safe software usage into the software.
The whole idea is to realize that Security plays its part in a DevOps process.
We can place a finger on marketing and financial environment as well-Organizations need to get more innovative and creative, by the day, to get customers at their fingertips. This means that software needs to be created, in tight schedules, to gain sales and market share, while meeting customer needs. Which means less time to give security consideration.
What are its ill effects if not implemented?
Though software may be aesthetically pleasing in design and caters to all needs of a user, all may not be rosy when the software is faced with a threat. Just as humans react in a variety of ways in a situation, anything other than acceptable or desirable behavior from the software is not welcomed.
Usual culprits such as zero-day vulnerability, code injection, hackers, etc. can work against the good of the software.
We can recall examples such as the Windows OS Zero-day vulnerability of 2019, which was caused by flaws in the Windows’ handling of Windows Meta File (WMF) and the Vector Markup Language (VML), which allowed attackers to exploit millions of systems.
The spear-phishing attack faced by Twitter in 2020 caused a massive data breach, ensuring non-confidentiality of personally identifiable information. This shows how security has a long way to be taken seriously by developer companies.
Here is where Secure Software Engineering comes into the picture-Defining the probability of software working in favor of an attacker if malware was injected? Was the software coded to behave like that? What are the measures within the software to counteract such a scenario? What countermeasures can be implemented by the DevSecOps team?
Stating DevSecOps philosophy, organizations should integrate security into every part of the DevOps life cycle, including inception, design, build, test, release, support, maintenance, and beyond. In DevSecOps, security is the shared responsibility of everyone in the DevOps chain.
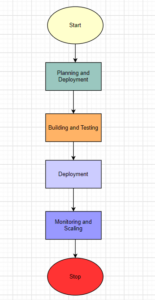
Cycles in a DevSecOps environment
Measures to implement security:-
-
Static application security testing (SAST)-Code Review for design flaw or incorrect error handling
-
Software composition analysis (SCA)-Provides remedy for vulnerability existence within source code
-
Interactive application security testing (IAST)-Analysis of UI response with a web application. Session hijacking, cookie stealing are common threats.
-
Dynamic application security testing (DAST)-Similar to IAST.
Benefits:-
-
Reduced costs in fixing the issue at hand
-
Real-time reporting
-
Accelerated remedial and patching
-
Fast delivery of patched software
-
Minimizing security bottlenecks
-
Tools for efficiency-By using tools that can scan code as you write it, you can find security issues early. Examples are static code analyzer or traditional peer review
-
Vulnerability Scanning and Runtime Protection
-
Raising awareness among the workforce for the need for App Security
- Carry out threat modeling — Threat modeling exercises can help you to discover the vulnerabilities of your assets and plug any gaps in security controls. Identify the riskiest events occurring across your infrastructure and build the necessary protection into your DevSecOps workflows.
- Meeting security compliance requirements-Security measures in software meeting standards such as MISRE and AUTOSAR
- Documentation-Cannot stress it enough
Parting Notes
From experience and reviews from online forums, people would rather have a secure application to use, rather than a shoddy app with backdoors doing malicious stuff on the backside.
Conclusion
People value convenience after all and if the software gets flak for not securing sessions or customer information, there would be no meaning for the fast delivery of code.
Correlating it with real life, people take security measures to protect their assets. If the same could be realized by developers, there would be fewer vulnerabilities, threats, and overall, fear to deal with.
View the Original Article HERE
